@Transactional

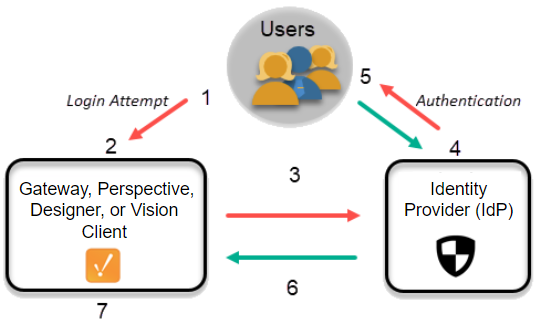
@Transactional When You Use @Transactional at the Class Level: All public methods of the class are automatically transactional, as if you had added @Transactional on each method. Public method ==> Runs within a transaction Private / protected method ==> Not transactional (no proxy interception) Internal method call ==> Not transactional (e.g., calling one method from another within same class) Spring AOP-based proxy ==> Only public methods are proxied and eligible for transaction management With Proxy (via @Transactional): Spring creates this proxy automatically when you use @Transactional. userService.updateUser(); Goes through proxy first: ...