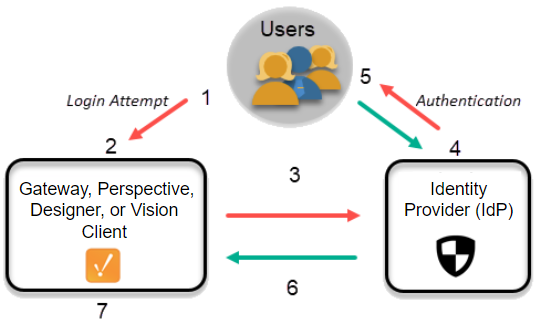
Popular Identity Brokers / Identity Providers 1. Auth0 (now part of Okta) Easy to set up and very developer-friendly. Supports social logins, enterprise identity providers, and custom databases. Offers built-in multi-tenancy, rules, hooks, and extensibility. Free tier available; widely used in startups and enterprises. 2. Okta Enterprise-focused identity platform. Strong integration with SAML, OAuth, OpenID Connect, and SCIM. Supports workforce and customer identity. Very powerful for large-scale enterprise SSO needs. 3. Azure Active Directory (Azure AD) / Entra ID Microsoft's identity platform. Ideal for organizations already using Microsoft 365 or Azure. Supports OAuth, OIDC, and SAML. Common in enterprise environments. 4. Google Identity Platform Allows federated identity through Google accounts. Can be used directly or as part of Firebase Authentication. Good for consumer-facing apps with Google users. 5. Firebase Authentication Developer-friendly from Google. Supp...